The scope of the VPN market report is divided into three categories: type, segment, deployment model and organization size. End users are also included. The report provides an overview of the global VPN market and analyzes the market trends, considering the academic year 2021 and forecast 2022-2030.
New York, July 25, 2022 (GLOBE NEWSWIRE) — Reportlinker.com has announced the release of the “Virtual Private Network (VPN): Global Markets” report – https://www.reportlinker.com/p06310247/?utm_source =GNW
Revenue forecasts based on segment type, delivery model and category, organization size, geography, and end users were calculated using values calculated from the manufacturer’s total revenue.
The report includes:- 50 data tables and 40 supplementary data An up-to-date overview of the global market for private networks (VPNs) in the Information Technology industry – Analysis of global market trends, with historical revenue market entry into 2021 Estimates for 2022 and 2023, and forecast compound annual growth rates (CAGRs) through 2027. Highlighting the market potential of private networks and project areas of this market in various segments and sub-segments. Real-time VPNs market size estimation, revenue forecast, and market share analysis based on combination of VPN type, segmentation pattern, organization size, end user, and geographic region – Analysis of key driving trends, issues, and opportunities in this unique market innovative, in addition to current trends, new developments, and regulatory influences on the market – In-depth information on increasing investment in R&D activities, major technology issues, specific industry issues, major user types end markets and the impact of COVID-19 on the growth of this market. Competitive landscape of leading private network players, and updated information on agreements, collaborations and product launches in the global VPN market – Company profiles outlining global leaders including Kape Technologies PLC, Nord Security, OpenVPN and Proton Technologies AG
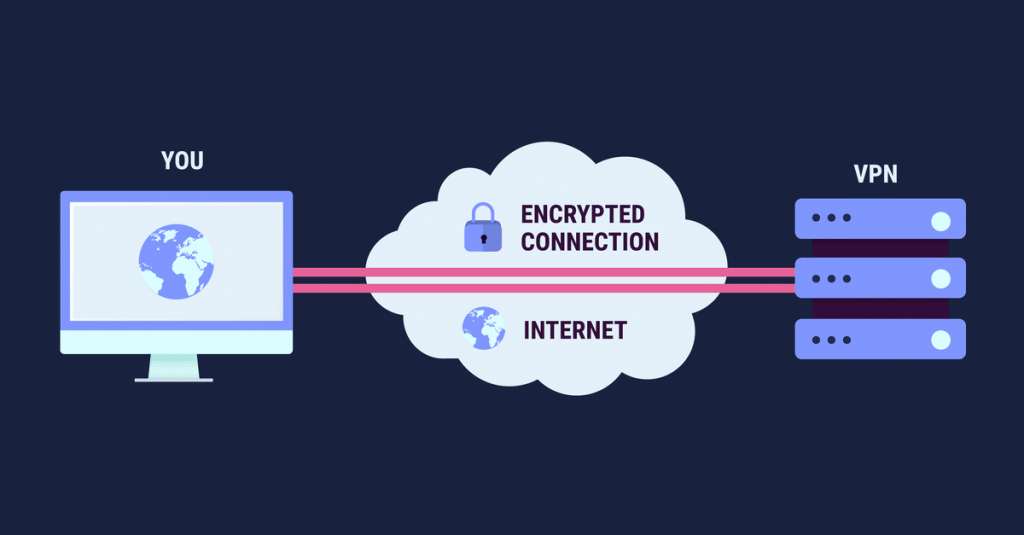
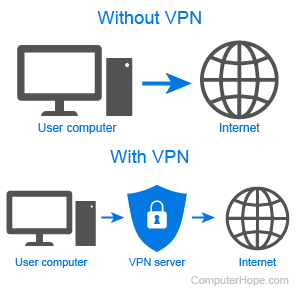
Summary: VPNs provide an anonymous connection between your computer and the Internet. This ensures that data and information remain confidential even when the network is accessible to the public.
Each type of encryption has its strengths and weaknesses, however all encryption tools succeed in encrypting user data so that it is useless to other users.
There are different types of VPN protocols or security methods. PPTP, point-to-point tunneling protocol, is one of the oldest tunneling methods, which is still used today but It is widely considered one of the least secure tunneling methods.
Other systems include Transport Layer Security, Secure Shell (SSH), Layer 2 Tunneling Protocol (L2TP/internet security) (IPSec), Internet Key Exchange Version 2 (IKEv2) and OpenVPN. Because OpenVPN is an open source protocol it is one of the most secure as any vulnerabilities in its software will be found and fixed quickly.
The increasing number of cyber attacks will fuel the growth of the VPN market in the coming years. According to the figures of Check Point Software Technologies Ltd., organizations around the world suffered an increase READACTED% of cyber attacks in the week of 2021 compared to what they did last year. The report also revealed that every organization experienced REDACTED cyber attacks every week around the world. According to the company, the cost of cybercrime could reach $READACTED trillion by 2025. Security has become an important practice in both the public and business sectors.
Large companies are adopting VPN technology because companies are more concerned about data security, which reduces cyber attacks on business operations. These cyber attacks include theft, fraud and destruction of data.
Therefore, the increasing number of cyber attacks leads to the growth of network protocols that allow companies to securely share their data online. This has led to an increase in demand for VPN solutions over the forecast period.
The global VPN market is segmented based on type, segment, delivery model and company size, end user, and geography. Based on type, the global VPN market is segmented into site-to-site VPN.
Based on segment, the global VPN market is segmented into software, hardware, and service. Based on organization size and scope, the global VPN market is segmented into large enterprises and small and medium enterprises.
The global VPN market is segmented based on deployment mode, which is cloud and on-premises.
Geographically, the market is segmented into North America, Europe, Asia-Pacific, and Rest of the World (including South America and the Middle East & Africa). Read the full report: https://www.reportlinker.com/ p06310247 /?utm_source=GNW
About ReportlinkerReportLinker is an award-winning market research solution. Reportlinker collects and organizes the latest industry data so you can get all the market research you need – instantly, in one place.
Why do I need a VPN?

The primary goal of a VPN is to hide your online activities. VPNs protect against hackers and hackers on public networks. However they also hide your IP address, browsing activity, personal data, and other information on any Wi-Fi network – even at home.
Why does anyone need a VPN? The main purpose of a VPN is to hide your online activities. VPNs are mainly used to protect against thieves and thieves on public networks, but they are also useful for hiding your IP address, browsing history, and personal data on any Wi-Fi network even at home.
Do I really need a VPN at home?
A VPN is highly recommended in all cases, especially when working with sensitive data. It is recommended that you use it at all times to protect yourself from data breaches, hacking, and leaks, as well as intruders such as ISPs and advertisers. VPNs protect your privacy and protect your data from hackers and other cybercriminals.
Does the average person need a VPN?
VPNs can be useful however they are not necessary for every user or in every situation, especially now that most internet traffic is encrypted with HTTPS the secure protocol whose origin appears at the beginning of most web addresses.
Why you should not use a VPN?
VPNs are not able to encrypt your traffic – it’s simply not technically possible. You cannot change the fact that the tool expects plain text. When you connect to a VPN, the only encrypted part of your connection is through the VPN provider.
Is VPN worth having?
The quick answer to this question is that investing in a VPN is worth it, especially when you are concerned about security and privacy while surfing the Internet. VPNs, or private networks, create a private network for a person’s computer while using a public Internet connection.
Why you shouldn’t use a VPN?
VPNs are unable to encrypt traffic Technically it is impossible. You cannot change the fact that the tool expects plain text. When using a VPN, the only part of your connection that is encrypted is through the VPN provider.
Is it worth using a VPN all the time?
VPNs provide the best security for online use, so you should keep your VPN active at all times to protect yourself from data leaks and cyber attacks, even when you’re connected to public Wi-Fi and as well as preventing third parties such as ISPs or advertisers. So always protect your VPN. When you go online, make sure you use a VPN.
What are the disadvantages of VPN?
Disadvantages of VPN
- #1: It is not intended for regular use. VPN remote access was never designed to connect an entire company to a WAN. …
- #2: Complexity hinders scale. …
- #3: Lack of security granularity. …
- #4: Unpredictable performance. …
- #5: Unreliable access.
What is the advantage and disadvantages of VPN?
Although it’s not always the best choice, a VPN is the safest and most cost-effective way to ensure your online security. Advantages of VPN. Certain activities that require high connection speed such as gaming may not be performed with a VPN however they can be easily disabled and enabled.
Are there any disadvantages to using a VPN?
Similarly using a VPN service has some disadvantages. Speed, performance, and price. A good encryption system will always cause delays. Using a VPN service can slow down your internet connection because of the processing power required for encryption.
What are two types of virtualization?
There are two options for virtualization: local and remote. Depending on business needs, remote or local desktop configuration is possible. However, the local desktop configuration has many limitations, including the inability to use mobile devices to access web resources.
What are the two types of virtualization in cloud computing? Different Types of Virtualization in Cloud Computing
- Server Virtualization.
- Application Processing
- Network Engineering.
- Desktop Virtualization.
- Storage Virtualization.
What is virtualization and its types?
Virtualization is “the creation of a virtual (instead of real) object, for example, desktops, storage devices, servers, operating systems or network resources”.
What is virtualization and types?
Virtualization is the process of separating service from physical delivery. It is the process of creating a virtual model similar to the hardware used in computers. It was first created during the common age.
What are the 3 types of virtualization?
Server virtualization is the use of software to separate the physical hardware of individual servers. Learn about the three main types of server virtualization: full-scale para-virtualization, and OS-level virtualization.
What is Type 1 and Type 2 virtualization?
The main difference between Type 1 and Type 1 hypervisors run on bare metal, while Type 2 runs on top of the operating system. Each type of hypervisor also has its own advantages and disadvantages and specific use cases.
What is a Type 1 virtual machine?
Type 1 hypervisor is installed directly on the underlying computer hardware and communicates directly with the memory, CPU, storage, and CPU. For this reason, type 1 hypervisors are also called metal hypervisors. A version 1 hypervisor replaces the host operating system.
Is VirtualBox Type 1 or Type 2?
VirtualBox is a type 2 hypervisor which is also known as a hosted hypervisor. A type 2 hypervisor is an app that runs on an OS that is installed on a host.
What are the 3 types of virtualization?
Server virtualization uses software to divide physical resources into individual servers. Learn about the three basic types of server virtualization: full-utilization, para-virtualization, and OS-level virtualization.
What are the 3 virtualization techniques?
To do this, three fundamental basic techniques for embedded systems are considered: full translation, abstraction (i.e. hardware-level processing), and containers (i.e. process- functional-level).
What is IPv4 and IPv6?

Share Article: Internet Protocol version 4 (IPv4) is a protocol designed for use in packet-layer networks (such as Ethernet). IPv4 has the capacity to handle up to 4.3 million addresses. IPv6 is more advanced than IPv4. It has better features.
What is IPv6 used for? Internet Protocol version 6 (IPv6) is the most modern version of the Internet Protocol (IP), a communications protocol that serves as an identification and location system for computers on networks and paths that connect the Internet.
Should I turn IPv6 on?
Internet Protocol version 6 or IPv6 (Windows Vista, Windows Server 2008, and later) is a required feature of Windows Vista and Windows Server 2008. We do not recommend that you install IPv6 or its components. If you do, some Windows components may not work. We recommend using IPv4 preference over IPv6 prefix policies instead of disabling IPv6.
What happens if I turn on IPv6?
IPv6 is a completely different network with different addresses. Enabling IPv6 can cause you to break your security devices or bypass them. For example, Linux port filtering is done using iptables. This only applies to IPv4 and you should use ip6tables to protect IPv6.
Is there a downside to enabling IPv6?
Con: It is difficult to put prefixes on IPv4 Topology Diagrams, and the shorter the length, the easier it is to add them to the topology diagram. But not so with IPv6, even with shorter rules that remove unnecessary zeros.
Which is better IPv4 or IPv6?
Internet Protocol version 6 (IPv6) has more advanced features than IPv4. It can provide an unlimited number of addresses. It replaces IPv4 to accommodate the growing number of networks worldwide and helps solve the IP address exhaustion problem.
Which is more reliable IPv4 or IPv6?
IPv4 does not have connection integrity IPv6 has connection integrity, while IPv6 has end-to-end communication. IPv6 is superior to IPv4 in terms of end-to-end connectivity. For MAC address mapping, IPv4 uses ARP while IPv6 uses NDP.
Why do we prefer IPv6 instead of IPv4?
IPv6 uses 128-bit Internet addresses. Therefore, it can support 2^128 Internet addressesa340,282,366,920,938,463,463,374,607,431,768,211,456 of them precisely. The number of IPv6 addresses is 1028 times more than IPv4 addresses
Which is better VPN or VDI?

VDIs are more efficient than VPN gateways and come with lower latency and bandwidth. They also tend to be efficient and effective in deploying public cloud environments. Initial costs for VDI are significantly higher than other VPN gateways for remote access.
Can VPN access my photos?
They can even see any non-personal information you have. For example, if you are posting something on an HTTP page, they will be able to see it. Photos, passwords, messages and more. Now, if you are using a VPN it will change the middleman.
What information can a VPN see? It depends on the VPN company you choose, but all VPN companies can see your internet traffic and history. Most VPN companies will choose to delete this information and redirect it to a file or folder for deletion. These are the so-called “no-log” companies.
Can VPN access my files?
The short answer is yes. A VPN is a network. It’s like connecting to a VPN. Administrators and users with the correct privileges can remotely access systems or view network files.
Can VPN access your phone data?
VPN usage is counted against the data limit of your tablets and smartphones. That’s because the data you receive from these devices must first pass through the servers of your mobile or internet service provider before reaching the VPN provider’s servers.
Can VPN access your phone data?
Your data limit on smartphones and tablets will be affected when you use a VPN. This is because the data you access using this device must pass through the servers of the mobile or internet service provider, before reaching the VPN provider.
Is VPN can access your data?
When you connect to public Wi-Fi networks that are accessible to the public, a VPN protects your data. The expert will only see confidential content and will not see or access your personal information.
Can VPN provider steal your data?
VPNs can infect your computer with malware and install hidden libraries. They will also access your personal information, make your information available to third parties, and even more.
Can VPN steal your data?
Some VPNs can infect your computer with malware, install hidden tracking libraries on your device, take your private information, leave your personal information accessible to third parties, and even steal your bandwidth.
Can VPN steal credit card info?
Not only that, but since they completely own the link they can also remove anything you type in, such as your home address, real name, phone number, and anything else they will need to disguise your identity. the internet.
Is VPN safe to use?
A reliable private network (VPN), can allow you to surf the Internet safely. A secure VPN can protect your IP and encrypt your internet history. It is increasingly used by government agencies to stop the slide. VPNs cannot guarantee your security in any case.
Does Samsung have a built-in VPN?
A built-in VPN client for Android (also known as StrongSwan) is available on all Samsung devices but, until now, has been limited to simple VPN configurations for specific devices. Samsung devices have an updated version of VPN Service for Android.
Do I need a VPN for my Samsung phone? You will need a Virtual Private Network if you travel to another country or connect to public Wi-Fi. This will secure your online activity and protect your data. Install Samsung Mobile VPN to keep everything safe.
Does my phone have a built in VPN?
Android comes with a built-in VPN client (PPTP, L2TP/IPSec and IPSec). Android 4.0 and above also supports VPN apps. You may need a VPN app (instead of a built-in VPN) for the following reasons: To configure a VPN using an enterprise mobility management (EMM) tool.
How do you know if you have a built-in VPN?
If you have a proxy/VPN setup, the black box will have four gray lines and one line. If you can’t see the box, it’s a sign that you don’t have VPN setup. Click here to connect/connect to an online VPN or proxy. You can also go to your settings, then click on network, then see if you are using a VPN/proxy.
How do I enable VPN on my phone?
How do I find my VPN on my Samsung?
Check if your VPN is already configured on your device by going to Settings > Connections > VPN > Additional settings. The VPNs already installed on your device will be displayed in this section.
C’est quoi VPN sur Samsung ?
Les VPN permettent aux appareils qui ne sont pas physiquement connectes reseau d’acceder a ce dernier en toute securite. Android includes an integrated VPN client (PPTP, L2TP/IPSec and IPSec). Les appareils equipped with Android 4.0 or later versions are also compatible with VPN applications.
Comment activer le VPN Android ?
Deroulez la barre de notifications, press Parametres a onnglet Connexions a Plus de reseaux VPN. Tap pour creer une nouvelle connexion VPN. Donnez un nom a cette connexion and l’address IP du connection server. Your new VPN connection is created.