Is Lenovo easy to hack?
Lenovo, the world’s largest PC maker, pre-installed virus-like software on laptops that makes the devices more vulnerable to hacking, experts said.
Can Lenovo be hacked? The ESET report said that more than 100 different models of Lenovo laptops with millions of users worldwide were found to have these vulnerabilities, which can allow attackers to launch UEFI malware. UEFI malware can be extremely stealthy and dangerous, ESET said in its report.
Is Lenovo a security risk?
Hundreds of Lenovo laptop models are facing security issues due to UEFI flaws. Lenovo has issued a security advisory about vulnerabilities affecting its Unified Extensible Firmware Interface (UEFI), which is loaded on nearly 100 of its laptop models. The affected laptops include the IdeaPad 3, Legion 5 Pro and Yoga Slim.
Which laptops do hackers use?
List of the Best Laptop for Hacking:
- Best Hacked Laptops: Top Picks.
- #1) Dell Inspiron.
- #2) HP Pavilion 15.
- #3) Lenovo IdeaPad.
- #4) ASUS VivoBook S.
- #5) Acer Aspire E 15.
- #6) Alienware m15.
- #7) Lenovo Legion Y545.
Is Lenovo Chinese spyware?
A review by the US Department of Defense (DoD) Inspector General in 2019 named Lenovo and Lexmark among the Chinese state-owned entities that threaten supply chain security and national security interests.
What do most hackers use to hack?
In addition to social engineering and disinformation, common coding techniques include:
- Bot networks.
- Browser hijacks.
- Denial of service (DDoS) attacks.
- Ransomware.
- Roots.
- trojans
- Viruses.
- Worms
What code do hackers use? Python. Python is probably the most popular high-level programming language used by hackers. It is object-oriented, which makes it faster to write.
Why do most hackers use Thinkpad?

Hackers love their ThinkPads. They are easy to work with, well documented and offer a lot of potential for upgrades. For the more daring, there is also a wide range of community-developed mods available.
Which laptop is mostly used by hackers? #1) Dell Inspiron Dell Inspiron is an aesthetically designed laptop that can be easily used by professional hackers to perform routine tasks. It has a 10th generation i7 chip that provides advanced performance.
Why does everyone use a ThinkPad?
ThinkPads have been widely praised for their superior keyboard quality on a laptop. ThinkPads were also the first to use a pointing stick for cursor movement, and some models have built-in key lights. In 1995, the “Butterfly” folding keyboard won awards for its unique design.
Can hackers be traced?
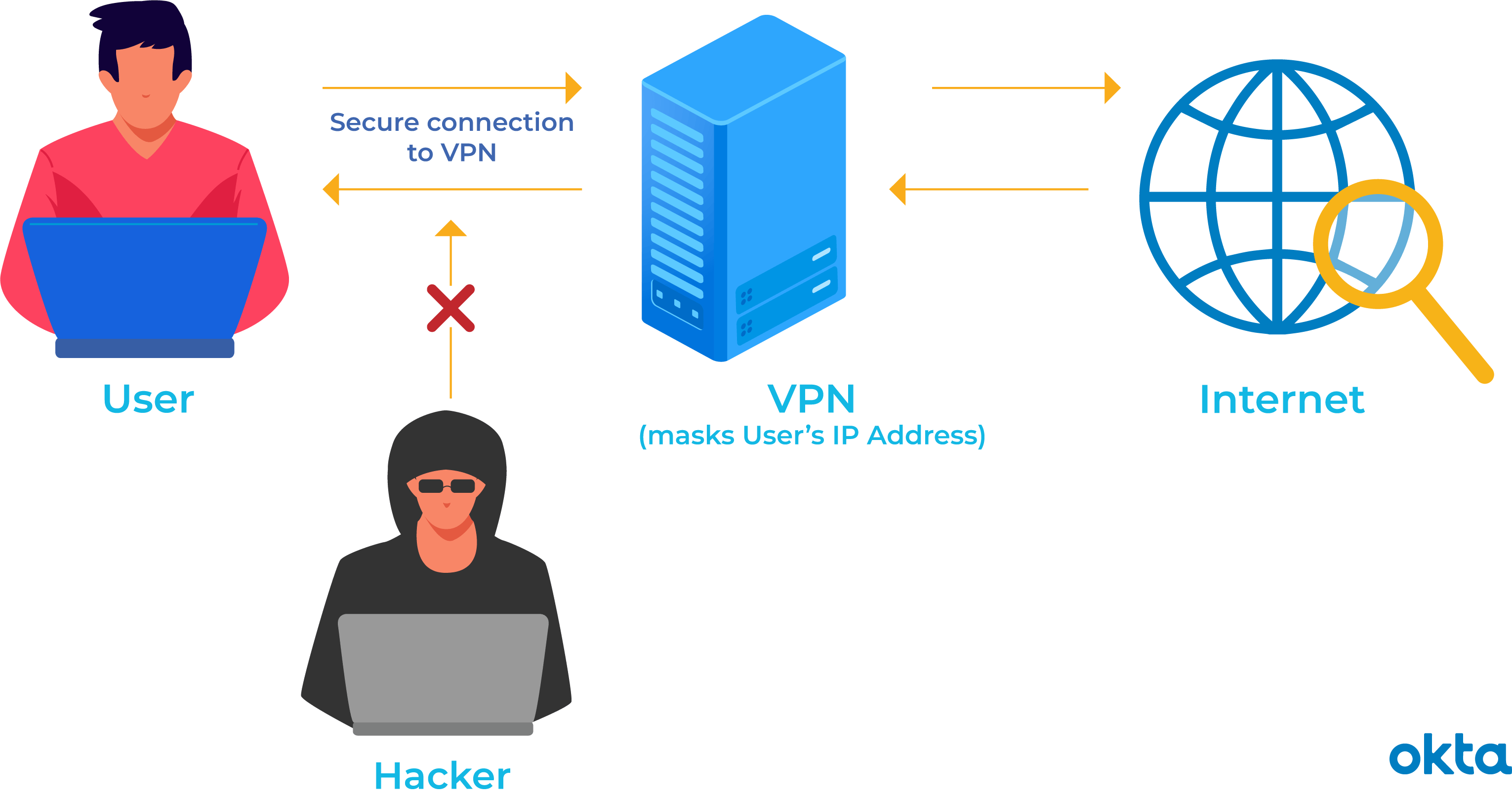
Most hackers will understand that they can be tracked by authorities identifying their IP address, so sophisticated hackers will try to make it as difficult as possible for you to find out their identity.
Can my phone be tracked by a hacker? By hacking or otherwise gaining access to the SS7 system, an attacker can track a person’s location based on cell phone mast triangulation, read their sent and received text messages, and log, record, and listen to their phone calls, simply by using their phone. number as an identifier.
How does a person know if they’ve been hacked?
Constant and Random Browser Pop-ups. Constant, frequent and random browser pop-ups are a common sign that you have been hacked. Especially if you’re getting random pop-ups while browsing websites that generally don’t show them, that’s a clear sign that your device has been compromised.
Is it easy to trace hackers?
Determining the identity or location of a cyber attacker is incredibly difficult because there is no physical evidence to collect or observe. Sophisticated hackers can cover their digital tracks. Although there are many different attribution techniques, the best approach utilizes more than one.
Can hackers track your IP address?
Track Your Identity and Location Ax cannot know who you are through your IP address. They can use it to find out who you are and see where you live. For example, your IP address is linked to your ISP, so criminals can use scams or cyber attacks to get your personal information from them.
