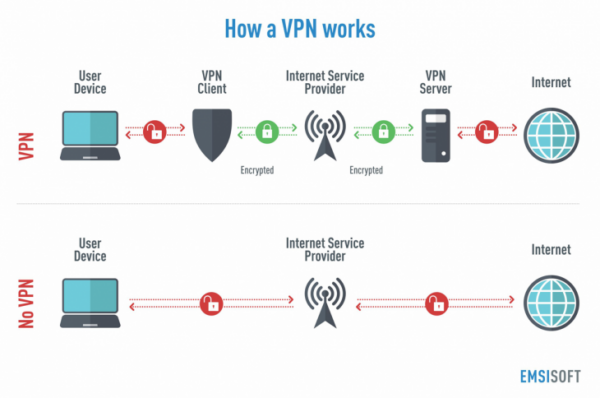
Your ISP can see all the websites you visit and keeps a history of your traffic just for this. However, using a VPN prevents that. Although browsing with a VPN prevents your ISP from tracking your movements, your ISP is probably not the only one the FBI is targeting.
Can hackers hear you?
We’ve been warned about hackers controlling the cameras on your computer screen, it’s still a concern, but hackers are also listening to you through your smart devices. The device itself may not be recording your conversation, but a hacker could be.
Can hackers hear your voice? Hacking with Inaudible Voice Neural Networks can ‘listen’ and process sound waves that are inaudible to humans. This means that hackers can potentially control your voice-activated assistant by playing your voice at an inaudible frequency.
Can hackers access your microphone?
It’s natural to worry about all this information being stolen. Not long ago, Edward Snowden confirmed that the NSA has the ability to hack into your phone’s camera or microphone — even if it is turned off – and take a picture of the user, or record his conversation. What the NSA can do, a hacker can do.
Can someone hack your phone and listen to you?
Yes. Unfortunately, they can even hack through the phone’s camera. But you can also learn how to block hackers from your Android or iOS phone. The first step is to understand how cybercriminals think and act.
Can hackers spy on you?
Generally, however, a tracker needs spyware installed on your device to compromise it. Hackers can access your phone physically, through apps, media files, and even emojis.
What happens when your phone is hacked?
If you find apps you haven’t downloaded, or calls, texts, and emails you haven’t sent, this is a red flag. It is possible for a hacker to steal your phone to send a call or text message or to spread malware to your contacts. Likewise, if you see a spike in your data usage, that could be a sign of hacking as well.
Can you get rid of the hacker in your phone? Fix a hacked Android phone with a factory reset Factory reset is a simple process that completely cleans your phone’s storage. A factory reset not only erases your photos, videos, messages, and other personal data, but also removes malware that lets hackers in.
How does a person’s phone get hacked?
Cyberattack on phones. Hackers don’t steal your phone and actually download malware—they don’t need to. Instead, they planted viruses on websites designed to infect mobile phones. They then get people to click on a link from their phone, which takes them to a website and a link.
Can hackers watch you through your phone?
Also, popular app developers are not immune from the suspicion of watching you through your phone’s camera. Generally, however, a tracker needs spyware installed on your device to compromise it. Hackers can access your phone physically, through apps, media files, and even emojis.
Can you tell if your phone is hacked?
Irregular performance: If your phone shows slow performance such as app crashes, screen freezes and sudden restarts, it is a sign of a hacked device. Unrecognized apps: If you notice some unrecognized apps downloaded on your device, it could be the work of a hacker.
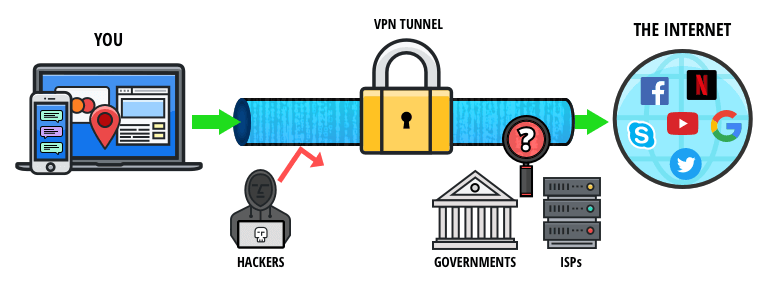
Can VPN steal your data?

Some VPNs will infect your computer with malware, install hidden libraries on your devices, steal your personal information, leave your information to third parties, and even steal your bandwidth.
Do VPNs collect your data? Yes, VPNs affect data usage, usually with an increase of five to 15 percent. However, some VPNs like Windscribe and Absolute Privacy claim that their VPNs only use about one to three percent more data, so This number is not valid in the industry. Do VPNs use cellular data?
Is VPN safe to use?
Using a secure private network (VPN) can be a safer way to browse the internet. VPN security can protect against IP and hide internet history and is increasingly used to prevent snooping by government agencies. However, VPNs cannot protect you in all weather conditions.
Can VPN steal credit card info?
Not only that, but because they completely own the connection and can grab just about any information you write down, including your home address, real name, phone number, and anything else they might need to look up. and you are online.