What problems would you like to solve in the next 12 months of your career? *
Do you know the name of your current provider(s) if you have set up a ZTNA or cloud-based SWG? *
If you haven’t already, what timeline are you working toward to transition your enterprise network to Zero Trust or SASE architecture? *
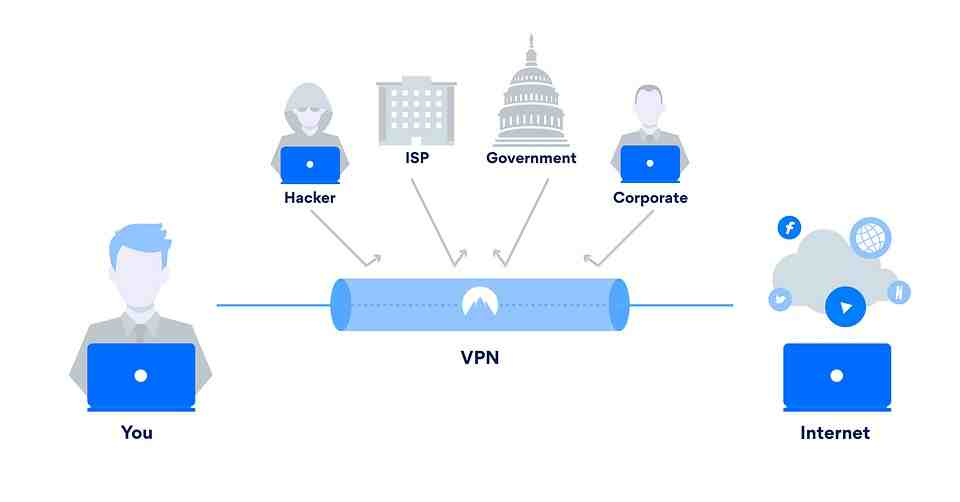
What is stronger than a VPN?
Tor is more effective than a VPN in the following scenarios: You want to be secure while accessing geo-restricted content. Using Tor is a good way to protect your privacy when trying to access content that is banned in your country.
Which VPN or Proxy is Better? Is a VPN Superior to Proxy Servers? Yes it is. VPN is superior because it offers security and privacy by routing your internet traffic through an encrypted VPN server and encrypting your traffic. A proxy is a proxy that simply sends your data through an intermediary server, but doesn’t necessarily offer any additional protection.
Is Tor as good as a VPN?
While VPN VPN protects your data through a network of servers managed by a centralized entity, Tor is a decentralized network run by volunteers. It’s slower, more complicated, more opaque, and far less efficient than a VPN. It’s still a powerful tool.
Can you be tracked on Tor?
Can Tor be tracked? It’s difficult, but possible. You should use a VPN to protect your privacy when using Tor. Some of Tor’s nodes have been compromised in the past and used to expose users and even hijack their traffic.
What is safer VPN or Tor?
While both Tor and VPNs are designed to protect your online privacy, VPNs are the most secure choice when used properly. Tor is a free browser that encrypts your requests, but it’s slow and doesn’t have access to all websites and can cause legal problems.
Which of the VPN is the strongest?
NordVPN is a fast and secure VPN service with a number of unique features. It’s one of the safest VPNs out there. It combines AES256 encryption with an ad and malware blocker. In addition, it offers dual VPN services, also known as multi-hop connections. NordVPN is the best choice for those who want to hide their online presence.
What’s the strongest VPN?
Most Reliable VPN Services for 2022:
- ExpressVPN. Most Reliable VPN Service in 2022 for Most Users – 5 Star VPN Service. …
- NordVPN. NordVPN comes second because of attractive security features. …
- Surfshark. Excellent, inexpensive VPN service that scores in all areas. …
- Private internet access. …
- Proton VPN. …
- CyberGhost. …
- hotspot sign
What is the strongest free VPN?
ProtonVPN is included in the list of the best free VPN services because it is a secure provider with no data caps. It is an open-source Virtual Private Network with an unlimited free version available on Windows, Mac, Android iOS and other devices.
What is more secure than a VPN?
Software-defined WAN (SDWAN) and Secure Access Service Edge are two of the most sought-after options. SD-WAN is an efficient alternative to VPN. SD-WAN can be a better alternative to implement point-to-point connectivity. It enables optimal routing of encrypted data between SD-WAN appliances in the network.
Can VPNs be hacked?
Their success relies on a combination of technical tricks, computing power, fraud, court orders, and behind-the-scenes persuasion. VPNs can be hacked, but it’s not easy. You are more likely to get hacked from using a VPN than if you don’t already have one.
What is the most secure VPN in the world?
Today’s Safest VPNs
- ExpressVPN. The most secure VPN available. …
- NordVPN. Amazing security and ease of use. …
- Proton VPN. Swiss security from top to bottom. …
- Surfshark. Affordable, effective and safe. …
- VyprVPN. This is a tiny VPN that doesn’t require impressive logging.
Is Tor safer than VPN?
While both Tor and VPNs are designed to protect your online anonymity, VPNs are the most secure option when used properly. Tor is a free browser that encrypts your data, but it’s not always fast and may not be able to access all websites. This can lead to legal problems.
Is Tor VPN Trustworthy? Tor is safe to download and use if you are an experienced user. It’s not 100% secure. There are numerous vulnerabilities that could compromise your privacy and security. For many people, these risks often outweigh the benefits of using a browser.
Can you be tracked with VPN and Tor?
Mostly, but not completely. The entry nodes in Tor can see your real IP address, but this can be thwarted by using Tor over a VPN. Using a VPN ensures that your IP address is hidden from all nodes. Your Tor activity is not tracked back to your precise location.
Can FBI track you on Tor?
Although the FBI has previously monitored Tor users, particularly in the Freedom Hosting bust last August, the McGrath operations offer a fresh perspective on his methods, including the sophisticated use of tracking software.
Can police track VPN and Tor?
It is impossible to monitor encrypted VPN traffic live. Using the Tor browser can be a red flag for your ISP and consequently for the police.
What is ZTNA in zscaler?
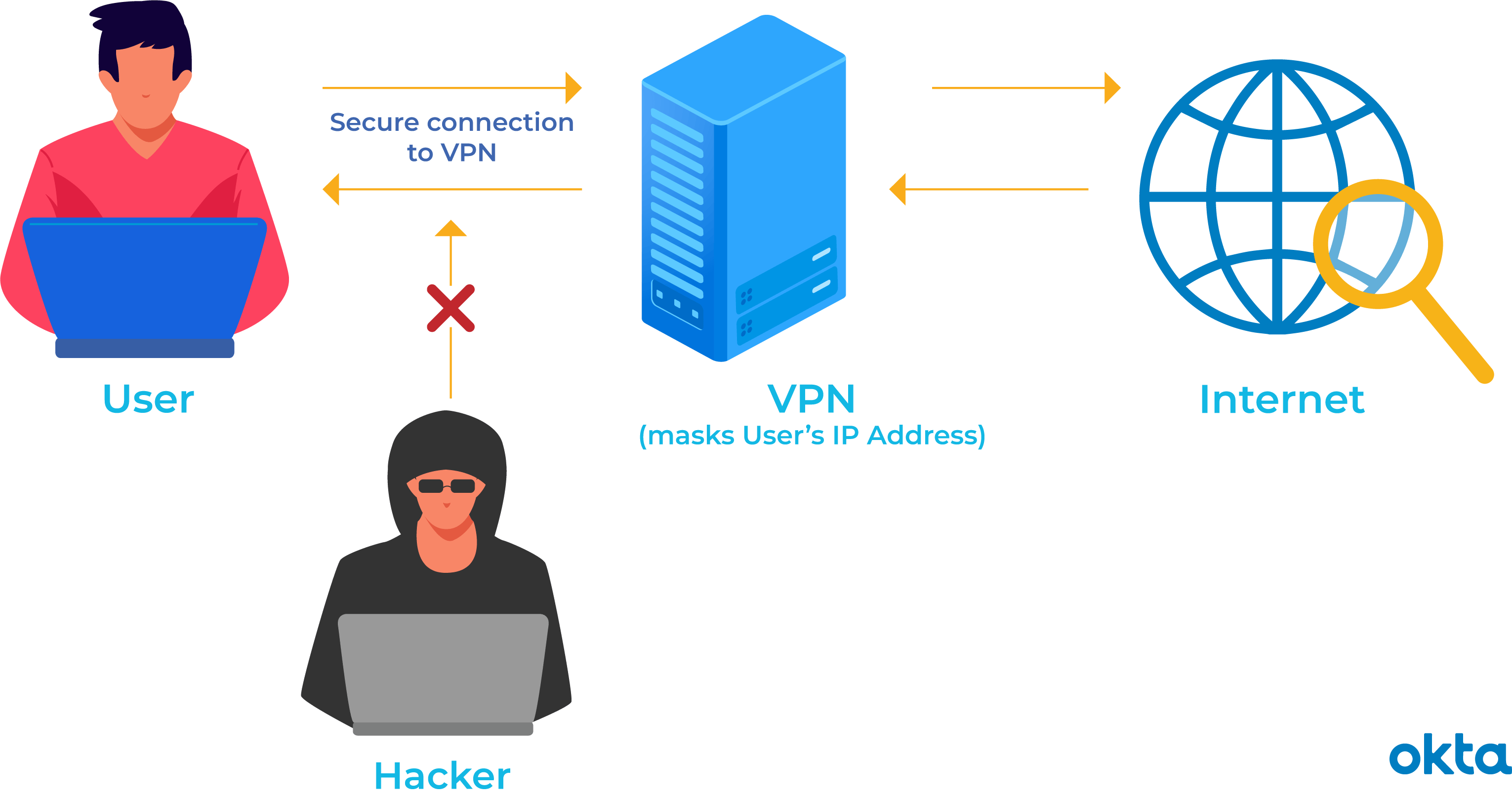
Zero Trust Architecture (ZTA): modernizing the federal government. Security from endpoint to application.
What does ZTNA stand for? Zero Trust Network Access (ZTNA) is an IT security solution that provides secure remote access to an organization’s applications, data and services based on clearly defined access control policies.
Is ZTNA a product?
Gartner estimates that 60% of businesses will replace their VPN with ZTNA services by 2023. This has resulted in ZTNA becoming the fastest growing Zero Trust product on the market, often becoming the starting point for IT leaders looking to adopt a Secure Access Service Edge (SASE) architecture.
What is the difference between VPN and ZTNA?
ZTNA connects users directly to private applications, unlike VPN, which reroutes user traffic through a corporate server. ZTNA discovered that while everyone tolerated VPN, nobody really loved VPN.
What is Fortinet ZTNA?
Fortinet ZTNA provides remote users with secure access to applications from anywhere.
What is the difference between VPN and ZTNA?
Unlike VPN, which requires user data to be backhauled through the corporate data center and slows down Internet performance, ZTNA connects users directly to private applications. The company found that VPN wasn’t a service that everyone liked.
Do you need VPN with zero trust?
Replace VPN with zero trust strategy
Is Z scaler a VPN?
Zscaler Private Access Zscaler Private Access: A VPN alternative that offers Zero Trust. Zscaler Private Access (ZPA) is a cloud-based Zero Trust Network Access (ZTNA) service that provides secure access to all private apps without requiring VPN remote access.
Why is ZTNA important?
ZTNA increases flexibility as well as agility and scalability. It enables digital ecosystems to function without making services directly available over the Internet. This reduces the risk of distributed denial of service attacks.
Is ZTNA a zscaler?
Zscaler has helped hundreds of the world’s largest companies adopt ZTNA. Our cloud-based ZTNA service has points of presence in hundreds of locations and uses some of the most advanced technology integrations to provide millions of authorized users with fast and secure access to private applications.
Is ZTNA better than VPN?
User satisfaction skyrocketed when using ZTNA compared to VPN Unlike VPN, which requires backhauling of user data through the corporate data center and slows Internet access speeds, ZTNA connects users directly to personal applications. The company learned that while everyone tolerated VPN, nobody really enjoyed VPN.
Is DuckDuckGo a VPN?
DuckDuckGo does not work as a VPN. However, it doesn’t track you in the same way as Google does. Also, incognito mode doesn’t protect your search history. By combining the DuckDuckGo application with a VPN, you can surf the Internet safely. It encrypts your internet traffic and secures your IP address.
Is a VPN Superior to DuckDuckGo? With a VPN, you can even bypass location restrictions and access blocked content like Netflix US, which DuckDuckGo cannot do even though it hides your IP address. If you want to guarantee your data security and have unrestricted access to the Internet via a VPN.
Is DuckDuckGo a proxy site?
DuckDuckGo includes a Tor exit enclave that allows you to search anonymously and securely from anywhere in the world. Enter! Proxy domain in DuckDuckGo automatically redirects you through a proxy, but proxy servers can be slow and even free proxies (like the one DuckDuckGo uses) are ad-supported.
Does DuckDuckGo share your IP address?
Searching the Internet with DuckDuckGo is completely anonymous. We never collect or share personally identifiable information in accordance with our strict privacy policy. We do not store IP addresses or other unique identifiers in our server logs.
Does DuckDuckGo hide IP address?
DuckDuckGo is not able to completely hide your identity online. Websites can still see your IP address. You can mask your IP address with proxy services like Tor. By combining Tor with DuckDuckGo, you can improve browsing privacy.
Does DuckDuckGo block your IP address?
Searching the web with DuckDuckGo is completely anonymous. In accordance with our strict privacy policy, we never collect or share personally identifiable information. We do not store IP addresses or other unique identifiers in our server logs.
Is DuckDuckGo truly private?
DuckDuckGo offers privacy-conscious browsing where you can surf anonymously and free from excessive tracking.
Can my IP be traced through DuckDuckGo?
What is DuckDuckGo? DuckDuckGo is described as “the search engine that doesn’t track your movements”. It promises not to use cookies to track users and claims that it collects no personal information about those who use it. Your IP address is hidden.
Can I be tracked on DuckDuckGo?
DuckDuckGo search is completely anonymous under our strict privacy policy. DuckDuckGo provides you with an empty search history for each search. It’s like you’ve never been there before. We do not store any information that searches can associate with you.
Does DuckDuckGo prevent tracking?
Online threats can be avoided DuckDuckGo protects your privacy at the search engine level, but not from other online threats. Individual websites or social media platforms may still track you and collect your information, and cyber criminals might target you with social engineering attacks.
Who can see your activity on DuckDuckGo?
Make sure you are using a reliable VPN. DuckDuckGo protects your browsing privacy, but it doesn’t protect against other internet threats like government surveillance and social media trackers. DuckDuckGo doesn’t encrypt all your internet traffic, which means anyone with access to your data can see your activity and IP address.
What’s another name for VPN?

| intranet | corporate network |
|---|---|
| internal network | private network |
| LAN | network |
How do I activate VPN? How do I turn off VPN on Android?
- Go to Settings > Network & Internet.
- Click VPN.
- Turn on VPN.
What are the 3 types of VPN?
VPNs can be grouped into three main categories: remote access, intranet-based site-to-site, and extranet-based site-to-site. Remote access VPNs are more common for individuals, while large corporations use site-to-site VPNs to protect their corporate networks.
Which type of VPN is best?
Many VPN experts recommend OpenVPN as the most secure protocol. The default encryption is 256 bits. However, other ciphers such as 3DES (Triple Data Encryption Standards), Blowfish (CAST-128) and AES (Advanced Encryption Standard) are also supported.
What is a VPN technical term?
VPN stands for “Virtual Private Network” and is a means of establishing a secure network connection while using public networks. VPNs protect your online traffic and hide your identity online. This makes it difficult for third parties to track your online activities and steal your information.
What is VPN in layman terms?
A VPN (Virtual Private Network) allows you to establish an encrypted connection to another network over the Internet.
Are SDP and ZTNA the same?
SDP is a security strategy that allows Zero Trust Network Access (ZTNA) and provides protection regardless of whether the service is on-premises or in a cloud. With SDP connectivity, it is based on the need-to-know model and “default denial” for all services.
What is the difference between VPN and ZTNA? Unlike VPN, which requires user data to be transported back through a corporate data center and slows Internet performance, ZTNA connects users directly to private applications. The company realized that VPN wasn’t a service that everyone liked.
Is ZTNA a SDP?
SDP (Software Defined Perimeters) and ZTNA (Zero Trust Networks Access) both leverage the concept of a dark cloud to prevent unauthorized users and devices from accessing applications and services to which they do not have access.
Is ZTNA a software defined perimeter?
Also referred to as a software-defined perimeter (SDP), Zero Trust Network Access (ZTNA) is a set of technologies and capabilities that provide remote users with secure access to internal applications.
Is ZTNA a zscaler?
Zscaler has helped hundreds of the world’s largest companies adopt ZTNA. ZTNA’s cloud-based service provides millions of authorized users with secure and fast access to private apps. It has points of presence in hundreds of locations.
Is SDP replacing VPN?
VPNs have traditionally been used to protect and manage corporate infrastructure. In some cases, an SDP could replace the VPN.
What is replacing VPN?
Two of the most common options are software-defined WAN (SD-WAN) and Secure Access Service Edge (SASE). SD-WAN is an efficient alternative to VPN. Rather than implementing point-to-point connectivity, SD-WAN provides the best possible routing of encrypted traffic between a set of SD-WAN appliances.
Why does SDP replace VPN?
SDP differs from VPN primarily in that it allows custom internal policies for network access, while VPNs are designed to provide users with unlimited access to resources and networks. VPNs also limit visibility across the IT network, while SDP allows it.
Is ZTNA part of SASE?
SASE, ZTNA and SASE. SASE is an advanced design philosophy similar to ZTNA. They are not different or competing network security models, rather ZTNA is part of a comprehensive SASE architecture.
What is ZTNA SASE?
The ZTNA security architecture is accessible to all users and devices at all times. It dynamically secures and connects devices and users to data and applications. Only authorized and authenticated traffic can access enterprise applications.
Is ZTNA a zscaler?
Zscaler has helped hundreds, if not thousands, of the largest companies around the world adopt ZTNA. ZTNA’s cloud-based service provides secure and fast access to private apps for millions of authorized users. Zscaler has points of presence in dozens of locations.