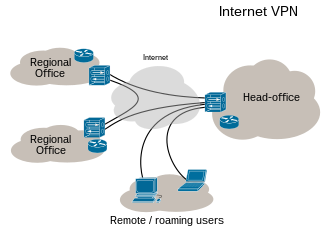
If you spend a lot of time on the Internet, you’ve probably come across the letters VPN. A virtual private network is something that even the most knowledgeable web users know about. You may have used a VPN to access geo-blocked content.
Get the latest technology news, analysis and trend spotting from around the world. Be the first to receive our latest stories, trend spotting and analysis. Get our weekly newsletter now.
Stay up to date with the latest engineering news. Just give us your email address and we’ll take care of the rest.
A Brief History of Private Networks: The Point-To-Point Tunneling Protocol
The roots of VPNs can be traced back to Microsoft in 1996 when its employees developed the Point-to-Point Tunneling Protocol, also called the Peer-to-Peer Tunneling Protocol or PPTN. This protocol was used to create a secure network between users by encrypting data and forming a tunnel over a LAN or WAN connection.
This protocol ensured that sensitive information could be transmitted securely over public networks. All you need to transfer data via PPTN is a username, password and server address. Because of this, it remains one of the most popular and easiest VPNs to use.
There are two forms of tunneling methods that are part of the PPTN, mandatory and voluntary. Voluntary tunneling is initiated by users and does not require the support of additional network devices or hardware such as routers. Forced tunneling, meanwhile, requires this support and is initiated by the server.
PPTN and other forms of VPN were mainly used in business environments to protect against data breaches before the early 2000s. But as the rest of the public gained access to the Internet and users began to transmit their own information online, VPNs became an increasingly popular method of protecting individual and personal data.
The Basics of VPNs: IPsec, SSL, and Mobile
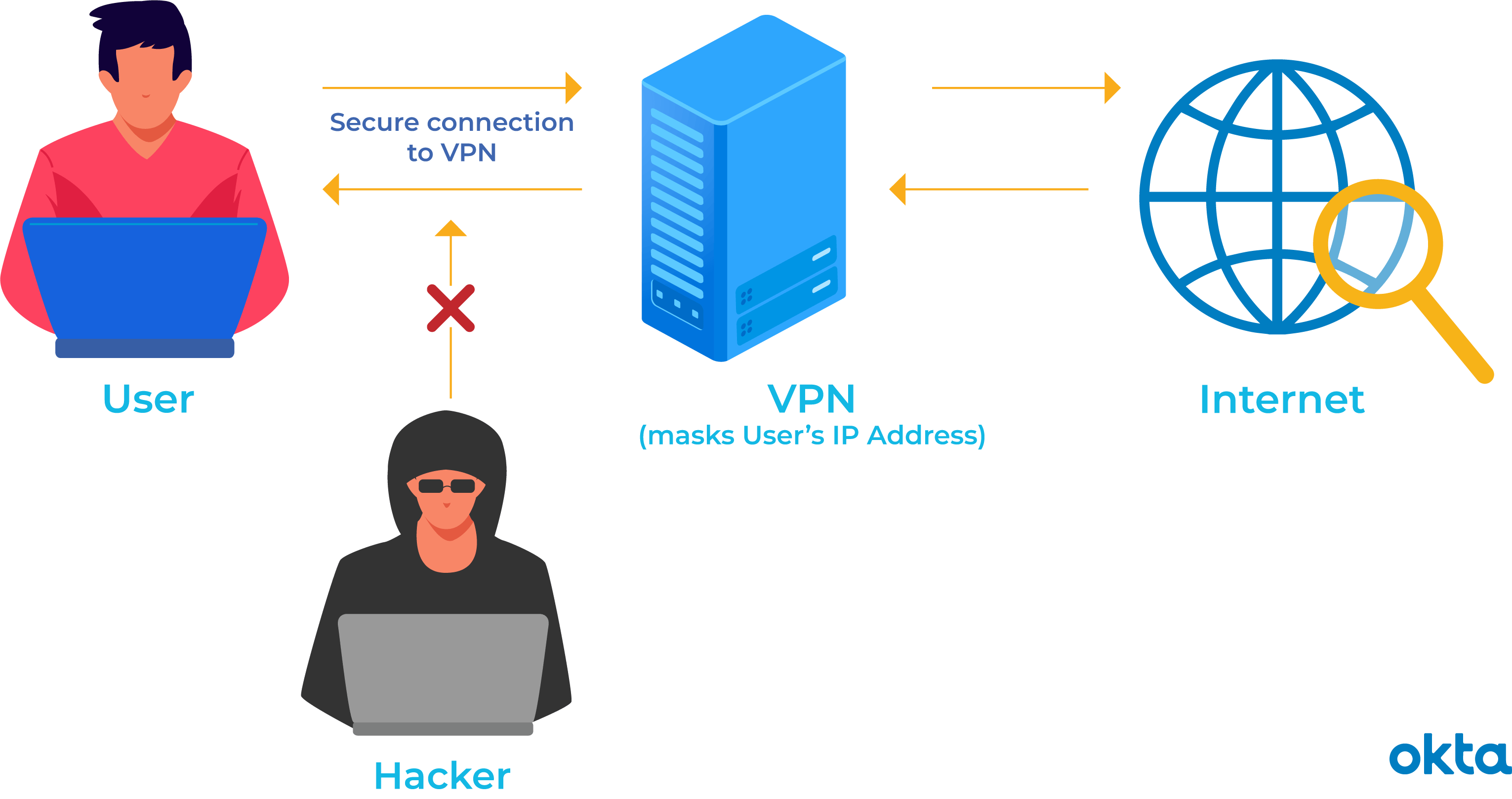
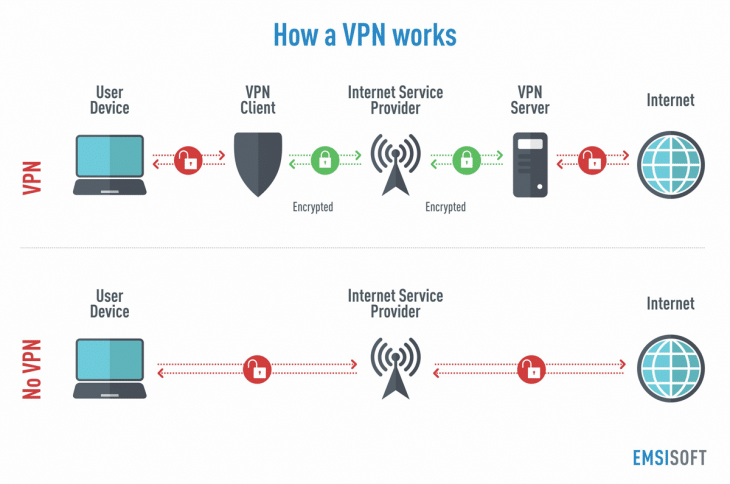
In the simplest terms, VPNs are a secure and private connection established by computers over the Internet. It is basically creating a private network within an existing network that allows users to transfer data securely. In simple protocols such as PPTN this is based on a three-step procedure involving encryption, tunneling and authentication.
The protocol creates a tunnel, which creates a network of users. Data is encrypted to ensure security. After receiving the data, the user must authenticate in order to decrypt the data. It is a simple and effective procedure that protects the user’s privacy at all times.
The most commonly used types of VPN today are SSL (Secure Socket Layer), IPsec (Internet Protocol Security), and mobile
You’ve probably already used Secure Socket Layer without even knowing it. SSLs are most commonly used in online shopping because they protect your payment information from falling into the wrong hands. Typically, the vendor must install an SSL certificate on their server to establish this network. This certificate must be obtained through the Certificate Authority and proves that the network is reliable.
This certificate is required to establish a secure connection between the browser and the server. Once the certificate is installed, sensitive data such as payment information can be securely transferred over the connection.
– Internet Protocol Security (IPSec)
You may be familiar with terms such as “IP” which refers to “IP address”. This is a reference to Internet Protocol, and IPSec is a way of securely transferring data over Internet Protocol networks. IPSec is the most widely used VPN method since SSL.
Similar to PPTP, IPSec follows a system of encryption and authentication. However, in the case of IPSec there are four steps. First, the data source is checked. It is then encrypted before transmission. After sending, the integrity and security of the data is checked to ensure that no one has changed the data. Finally, packets that detect errors are received twice or more times to protect against the possibility of a denial of service.
Mobile VPNs are exactly what they sound like: private networks for mobile phones. They can be used over wireless connections or in situations where you are moving between ranges. They work with a higher level of data compression than other VPNs, which means they use less battery and memory.
You enjoy all the benefits and flexibility of a VPN, but with the flexibility of a VPN, but optimized for use on mobile devices.
Why Use VPNs?: Protection and Play
By now it probably makes sense why VPNs are a good idea for working from home or other situations where you handle sensitive data. Telecommuting is feasible because employers can provide employees with secure access to company information online.
Using a VPN will also make you less visible to potential hackers because you won’t be showing up on public networks. This allows you to continue with your business without becoming a victim of a data breach or someone tampering with your data.
It’s important to keep in mind the next time you’re using the Wi-Fi at your local bar or coffee shop – anyone else using the network can, if they want to, access your personal information or device if they want to. Use a VPN to protect yourself.
Another reason to use a VPN is to allow access to content and media that you wouldn’t otherwise be able to see. You can cheat geo-restrictions by using a VPN to make it seem like you’re somewhere you’re not. This happens because your IP address has been changed to the address of your VPN. If you’re in Europe and want access to US Netflix, you can simply buy a US VPN and get a new digital library. If certain YouTube content is blocked in your country, you can use a VPN to access it.
There are many free VPNs online that can make the Internet a safer and potentially more exciting place for you. It’s definitely a great idea to try them out, especially if you travel a lot or use public networks a lot. Take care and have fun surfing!
Its success is due to a combination of technological tricks, computing power and court orders. Although VPNs can be hacked, they are difficult to hack. You are much more likely to be attacked by a VPN than if you don’t have a VPN.
Which country VPN is fastest?

| Earth | Average download speed (mbps) | VPN ban |
|---|---|---|
| Taiwan | 85.02 | Not |
| Singapore | 70.86 | Not |
| Sweden | 55.18 | Not |
| Denmark | 49.19 | Not |
What is the fastest VPN for torrenting? Based on the latest tests, the most reliable VPN for torrenting is NordVPN. NordVPN has the fastest download speeds and the most secure apps to protect your data without leaking. NordVPN is currently ranked as the fastest VPN offering speeds of 445Mbps.
Which country VPN server is fastest?
1. South Korea. South Korea is ranked #1 in terms of average connection speed and #3 in terms of peak connection speed.
Which country server is best for VPN?
Here’s our list of the best server countries to choose from when connecting to your VPN:
- Iceland. Iceland is our top pick among the best VPN server hosting countries because of its strict internet privacy laws. …
- Estonia. …
- Canada. …
- Germany. …
- United Kingdom. …
- Malaysia VPN. …
- Switzerland VPN. …
- VPN USA
Which is the fastest VPN server in the world?
Hotspot Shield is the fastest VPN in the world. To win this award, Hotspot Shield outperformed competitors in international and local testing conducted by Ookla(r).
How can I tell if my boss is monitoring my computer?
These are ways you can tell if your employer is monitoring your computer.
- Look for Suspicious apps in the Application Manager. …
- Look for suspicious background processes. …
- Check data usage for suspicious activity. …
- Look for suspicious programs. …
- Check your firewall settings.
Does my employer have the right to monitor my work computer at home? As a general rule, when you use your employer-provided equipment while on your employer’s network, your employer has the right to monitor any activity you do, regardless of whether you are working remotely or on-site. It is your employer who provides the communication technology and therefore has the right to monitor your activities.
How can I tell if my computer is being monitored at work 2022?
Right-click the taskbar and select Task Manager. Find the program monitoring your computer by clicking on the Process tab. You may want to check out a top tracker to determine the name. If you come across an identical name, you are being monitored.
Can you tell if someone is monitoring your computer?
If your computer at work has Windows, it is possible to see in Task Manager whether it is monitoring the computer. Right-click the taskbar and select Task Manager. Select the process monitor on your computer from the Process tab.
How do I detect monitoring software?
All ports that are open can be checked by going to Start. Click on “Allow this feature or program through Windows Firewall” on the left side of the box. This will open another box and you will be able to see a list of apps with checkboxes next to them.
Can I tell if my computer is being monitored?
Searching for suspicious processes You can identify suspicious processes by opening the Windows Task Manager. After you have started Windows and loaded Windows, press Ctrl Del to open the Windows Task Manager. Scroll through the list of active processes and look for suspicious ones.
Can you tell if someone is monitoring your computer?
If your computer at work is running Windows, it is possible to check whether the computer is being monitored from the Task Manager. Right-click the taskbar and select Task Manager. On the Process tab, find a program that may be monitoring the computer.
Can someone access my computer remotely without me knowing?
There are two ways that someone can gain access to your computer. Someone in your family or a student at work physically logs into your phone or computer while you’re not there, or someone accesses your computer remotely.
How VPN is created?
A VPN is a point-to-point virtual connection created using dedicated circuits or protocols for tunneling over existing networks. A VPN that can be accessed over the Internet could provide the same benefits as a wide area network (WAN).
Where was VPN first invented? The PPTP protocol was developed by a Microsoft employee in 1996. This was the first time VPN technology was implemented. The protocol provided an additional secure private connection between the user’s device and the Internet.
Can I create my own VPN?
There are many options available for hosting your VPN. For personal use, you can run the software on a cloud network server that is virtual. All cloud providers, from giants like Amazon Web Services to smaller operations like Vultr that offer cloud-hosted servers called VPSs.
Is making your own VPN worth it?
The short answer is yes. A VPN is a smart investment, especially if you’re concerned about your online privacy and security while surfing the web. VPNs, or Virtual Private Networks, establish a private network for one’s computer while connecting to a public Internet connection.
How much does it cost to build your own VPN?
How much does it cost to build a VPN that needs to be built? Setting up your VPN will cost between $5 and $10. This primarily includes the cost of renting a cloud server. The rest of the process is simple and free.
Who controls the VPN?
The person or company that operates the server is called the VPN Provider. Your VPN provider probably falls into one of these categories: Workplace: Your workplace may have a VPN server that allows you to securely and remotely connect to your workplace network.
How is a VPN managed?
Data is sent from your client to a point in your VPN network. A VPN point encrypts your data and sends it over the Internet. The second point in your VPN secures your data and then sends it to the correct Internet source such as an email server, web server, or your company’s intranet.
Is VPN private or public?
A virtual private network, also known as a VPN, allows you to ensure your privacy and anonymity online. It is built from an internet connection that is public to create an encrypted network. VPNs mask your Internet Protocol (IP) address, ensuring that your online activities are virtually untraceable.
Can VPN steal credit card info?
Not only that, but since they fully own the connection, they can review any information you enter, including your home address, real name, number, and anything else they need to impersonate you online.
VPNs can steal your data. VPNs can infect your computer with malware and install hidden tracking libraries on it. They can also access your personal information, expose your information to third parties and even take over your bandwidth.
Is it safe to make purchases on VPN?
Yes, it is safe to use a VPN when doing your online banking. To protect your data from hackers, use a VPN whenever you travel and connect to public Wi-Fi at a coffee shop, hotel or restaurant.
Can VPN steal bank details?
When you use a VPN, you will: VPN, you will: Stay safe on public WiFi a Unsecured public WiFi networks (like when you’re at the mall or at work) are vulnerable to cyberattacks. VPNs hide your bank login, password, and any other information you enter on the bank’s website or app to ensure hackers can’t access or steal your information.
Is it safe to make payment on VPN?
Without a VPN, hackers could gain access to your transactions and sensitive information, such as bank details and names, to gain access to your identity or access to your money. Your traffic will be encrypted using a VPN. This will prevent your transactions from being viewed by prying eyes.
Does iPhone have built in VPN?
Short answer: No. The iPhone does not come with its own built-in VPN and Private Relay is certainly not the answer to this. It is important to remember that this is the case for all Apple devices.
Should VPN be enabled on my iPhone? A VPN is a background application that protects your device, just like an antivirus. However, this is not always practical so we would recommend at least turning on iPhone VPN in those scenarios where your connection is more vulnerable. And, of course, if you want to get American Netflix from abroad.
How do I know if VPN is on iPhone?
You can also go to your settings app, then click on network, then check if you are using a VPN/proxy. It’s harder to check on Android/iPhone and doesn’t actually happen on the device. Check with your IT department if your WiFi is equipped with a proxy or VPN.
Does my iPhone automatically have a VPN?
In iOS, iPadOS, and macOS, VPN on Demand allows Apple devices to automatically establish a connection as needed. It requires an authentication method that does not require any user interaction such as certificate-based authentication.
How do I turn on VPN on my iPhone?
Go to Settings > General > VPN > Add VPN configuration type. You can choose between IKEv2, IPSec or L2TP (which includes IPSec encryption although it is not explicitly stated).
What is VPN on an iPhone?
VPNs protect the connection between your iPad or iPhone and the Internet. This helps protect your privacy by preventing your ISP (and anyone else!) from seeing what websites you visit. It also helps make you anonymous to websites, meaning they can’t track or trace you (unless you log in to them).
Does iPhone have a free VPN?
Top 5 Best Free VPNs for iPhone: Surfshark Best Free VPN for iPhone with Unlimited Connections. Atlas VPN is a reliable and free VPN service. ProtonVPN is an extremely fast and secure VPN for iPhone. Windscribe is a great free VPN option for iOS.
Do iPhone have built in VPN?
Does the iPhone have a built-in VPN? The short answer is no. The iPhone doesn’t have its own built-in VPN and Private Relay is certainly not the answer to this. It is important to note that this is the case with all Apple devices.
What is VPN and why do I need it?
VPN stands for Virtual Private Network. A VPN is an encrypted server that hides your IP address from companies, government agencies, and other hackers. VPNs protect your identity even when using public or shared Wi-Fi. Your data will remain secret from prying eyes.
Do you really need a virtual private network (VPN)? VPNs are key tools for protecting your personal data while browsing. It offers a fast, secure service that preserves your anonymity. VPNs allow you to securely connect to public Wi-Fi networks and encrypt your data.
Do I really need a VPN at home?
A VPN is highly recommended in all cases, especially when dealing with sensitive data. It’s essential to keep it on all the time to protect yourself from data intrusions, hackers and data leaks, as well as intrusive snoopers like ISPs and advertisers. VPNs protect your data and protect your privacy from third-party advertisers and cybercriminals.
Do I need a VPN in 2022?
VPNs have been protecting our online privacy ever since. A virtual private network allows you to browse anonymously and not be blocked by geo-restricted content and keeps your data safe.
Why you should not use a VPN?
VPNs cannot magically encrypt traffic. It’s technically impossible. You cannot change the fact that the server expects plain text. When you connect to a VPN, the only encrypted part of the connection is the one from you to the VPN service provider.
Should the VPN be on or off?
VPNs offer the best online security. It’s key to use a VPN to protect yourself from data leaks when using public Wi-Fi and to protect yourself from intrusive spies like ISPs and advertisers. So always keep your VPN on.
Why you should not use a VPN?
One reason not to use a VPN is when you’re gaming or downloading, as a VPN can sometimes slow down your connection speed. You can also pause your VPN when you want to access content that is not available in your region.
Why does my iPhone say VPN?
If you see the VPN logo in the upper right corner of your phone screen, it means you have an active VPN connection. The VPN program can be configured to start automatically when you turn on the phone, or you may have activated it yourself.
What are the main reasons for using a VPN?
The main purpose of a VPN’s main function is to hide your online activities. VPNs are used to protect against hackers and spying on public networks. However, they can also hide your IP address, browsing history, personal information and other data on any Wi-Fi network, even at home.
Are VPN a waste of money?
The short answer is yes. A VPN is a good investment, especially if you want to protect your online privacy and security while surfing the web. VPNs, also called virtual private networks, allow users to create an encrypted network on their computer using a public Internet connection.
What does VPN Do Reddit?
What is a VPN used for? The basic idea is that people don’t want others to see what they’re doing online, even if they’re not doing anything wrong. A VPN (virtual private network) is an internet security subscription that lets you set your own rules for using the internet.
Sources :