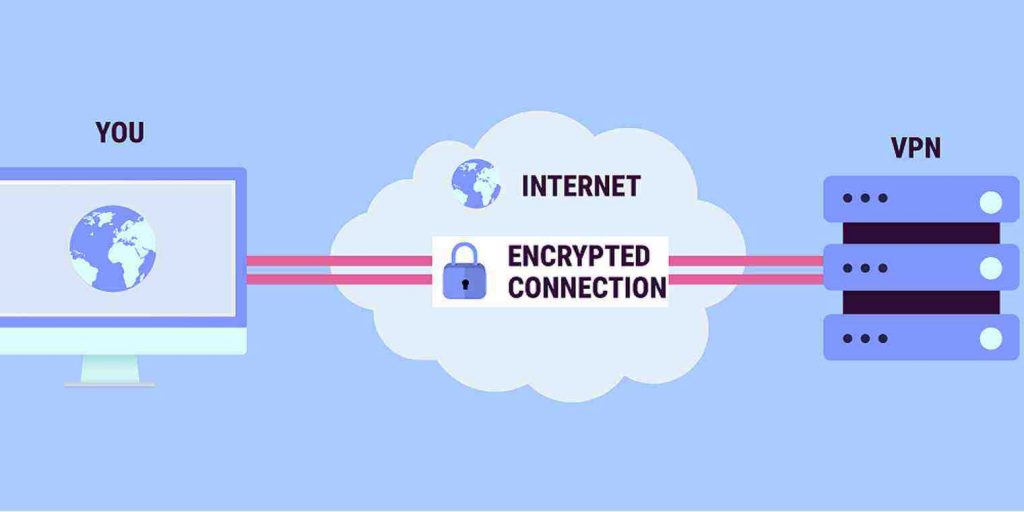
What technology should you set up on the network to prevent man in the middle attacks?

VPN. One of the best practices for network security is to use a VPN (virtual private network) when connecting online. A VPN encrypts the data you send online. This encryption stops the MITM attack from infiltrating your network traffic.
What commonly used computer programs are susceptible to man-in-the-middle attacks? 7 types of man-in-the-middle attacks
- IP spoofing. Every device capable of connecting to the Internet has an Internet Protocol (IP) address, which is similar to the street address for your home. …
- DNS spoofing. …
- HTTPS spoofing. …
- SSL hijacking. …
- Email removal. …
- Wi-Fi eavesdropping. …
- Steal browser cookies.
What prevents man-in-the-middle attacks?
Best practices for preventing man-in-the-middle attacks Having a strong encryption mechanism on wireless access points prevents unwanted users from joining your network just by being nearby. A weak encryption mechanism can allow an attacker to brute-force his way into a network and attack the man-in-the-middle.
What type of authentication can prevent a man-in-the-middle attack?
Phishing-resistant multi-factor authentication (MFA) can prevent man-in-the-middle attacks that rely on stolen credentials.
Can VPN hack your phone?

You can never know exactly how secure a wireless network is, and connecting to it is often a leap in the deep end. In any case, it is important to protect yourself against these intrusions, for example with a VPN connection. This way you enjoy mobile VPN security and it is almost impossible to hack your data.
Does VPN keep your phone safe? VPN software lives on your devices – whether that’s a computer, tablet or smartphone. It sends your data in a scrambled format (this is known as encryption) that is unreadable to anyone who wants to intercept it.
Can VPN access your phone data?
When using a VPN, count against the data limits on your smartphones or tablets. That’s because the data you access through these devices must first travel through your Internet service provider’s or mobile provider’s servers before reaching your VPN provider’s servers.
Why do hackers use VPN?
Hacking into a VPN connection involves one of two tactics. A hacker can either break the encryption through known vulnerabilities or steal the key through unethical means. Cryptographic attacks are used by hackers and cryptanalysts to recover plaintext from their encrypted versions without the key.
What does VPN not protect against?
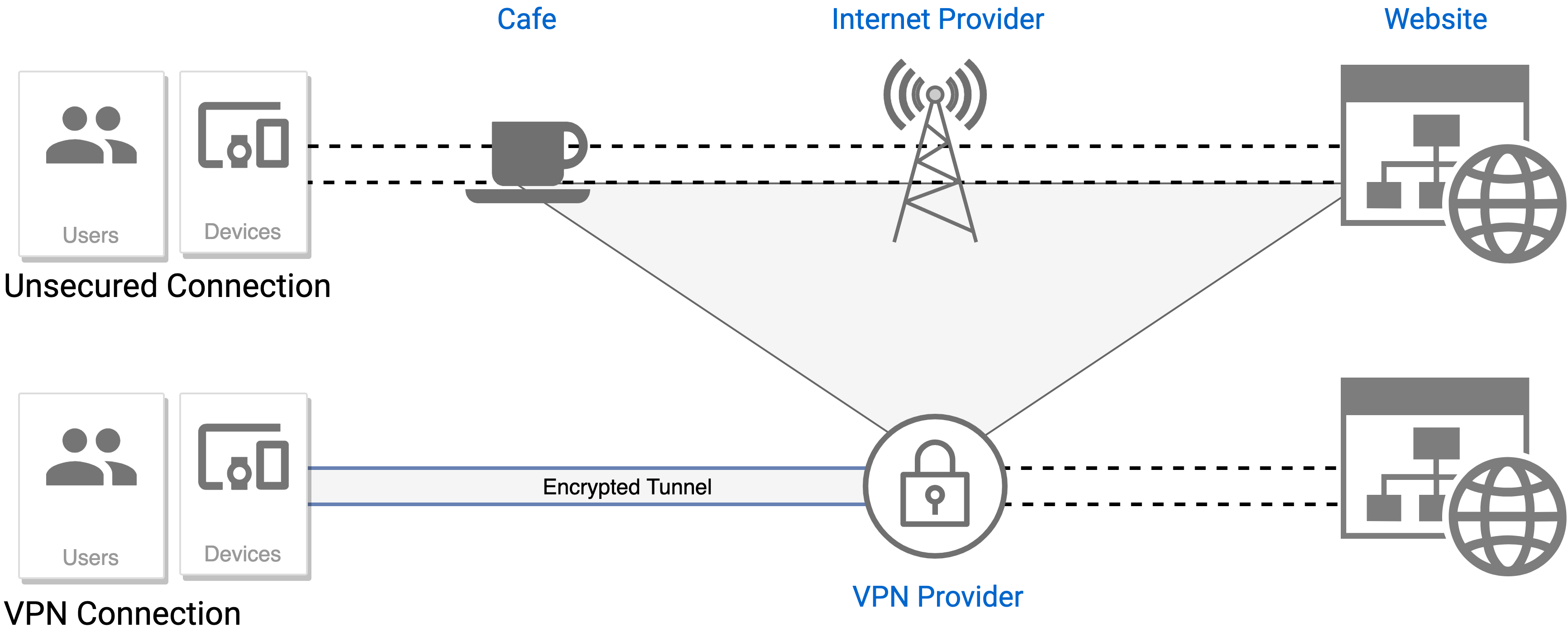
It’s important to remember that VPNs don’t work the same way as comprehensive anti-virus software. Although they protect your IP and encrypt your internet history, but that is as much as they can do. They don’t keep you safe, for example, when you visit phishing websites or download compromised files.
Does VPN Prevent Spying? Use a VPN – Although a VPN cannot prevent spyware from being downloaded to your device, it can mask your location and prevent your online behavior from being tracked and monitored. The best VPNs also have anti-malware and ad-blocking software, like CyberGhost.
Can VPN protect you from hackers?
How does a VPN prevent hacking? By redirecting your internet traffic to disguise your IP address, it makes it impossible to track you. And by encrypting the information you send over the Internet; it prevents anyone who intercepts your information from reading it. That includes your ISP.
What can a VPN not do?
A VPN could encrypt data between two points, but if your authentication information is not secure enough, a hacker could get in and start looking for data or committing fraud. A VPN will do nothing to protect your team from phishing attacks – phishing is on the rise because it’s cheap and effective.